DATA INTEGRATION FOR YOUR
SAAS APPLICATIONS
CONVAYR is the no-code integration platform (iPaaS)
that connects data from applicationto application
DATA INTEGRATION FOR YOUR SAAS APPLICATIONS
CONVAYR is the no-code integration platform (iPaaS) that connects data from application to application
CONNECT YOUR APPS
Select any source with any target application. Syncronize data both ways.


BUILD INTEGRATION WORKFLOWS
Move and transform data between applications, with full support for custom source and target configurations

MAKE YOUR DATA MOVE
Scheduled, real-time and dependent workflow automation.
Authorise anyone in your business to trigger workflows by email command or .csv.
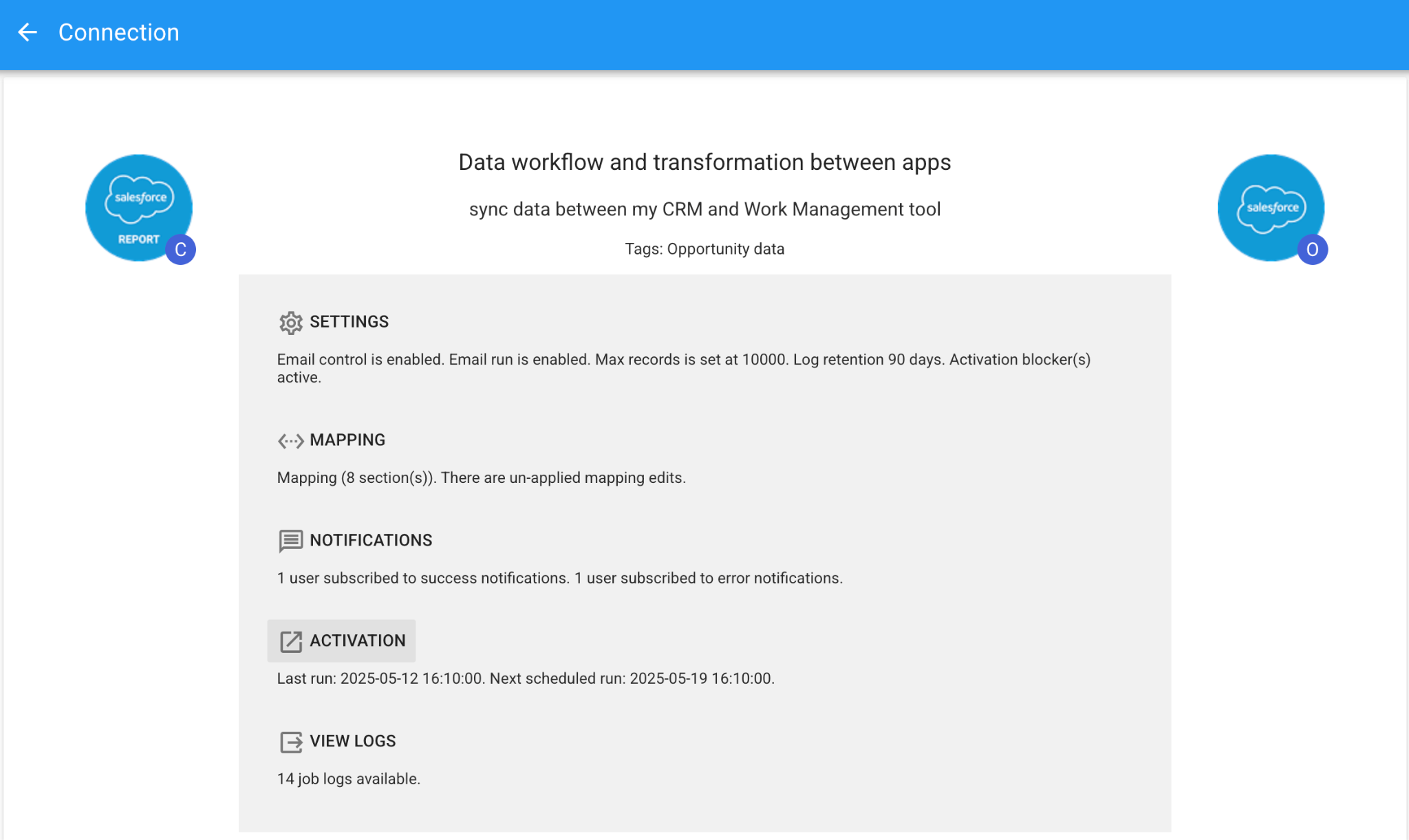

OPTIMISE WORKFLOW OUTCOMES
Track the status of your connections with configurable error management, logging and email notifications.

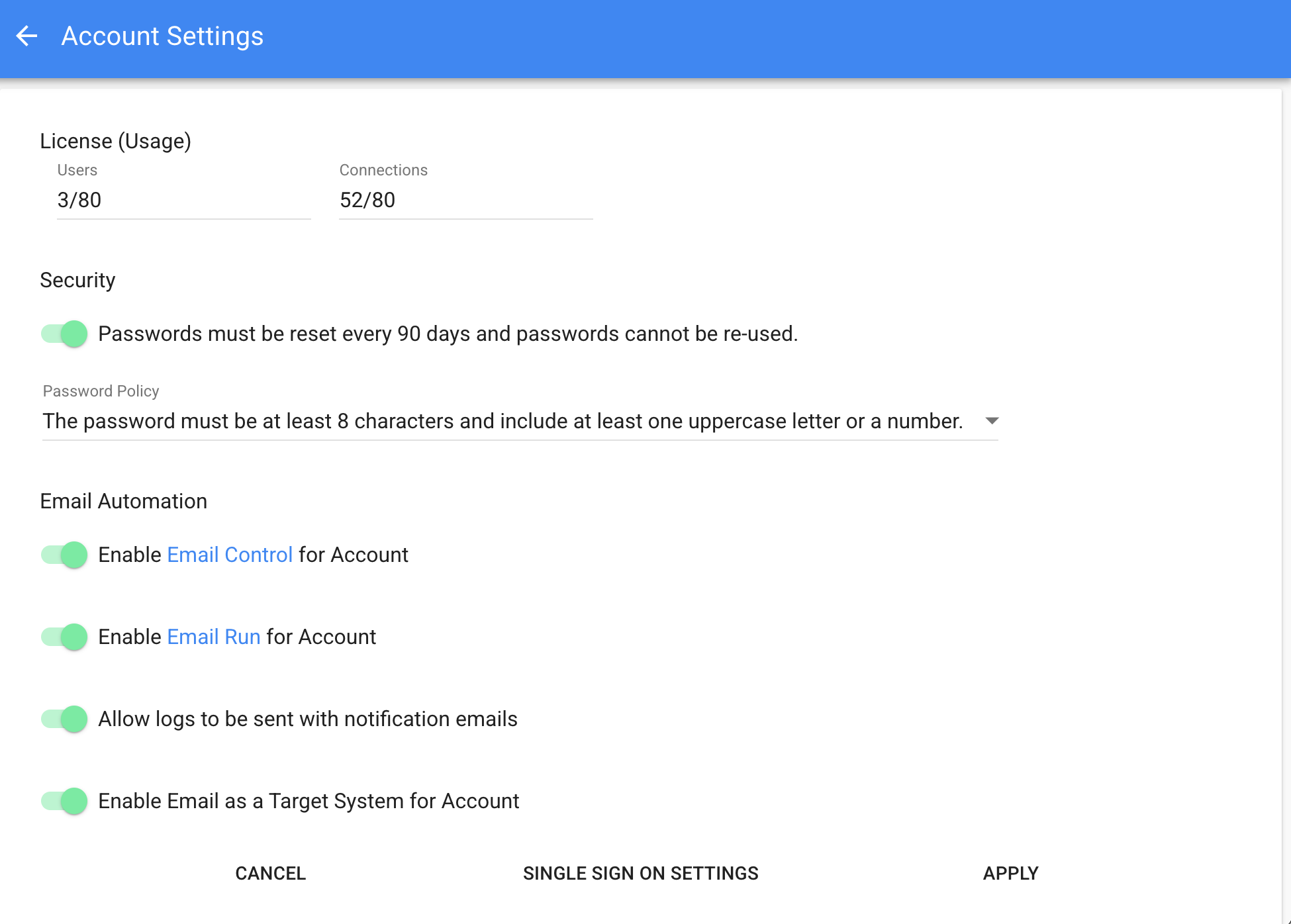
SCALES WITH YOUR BUSINESS
Manage users access to different integrations.
Meet the security needs of your organisation with SSO, password policies and secure credentials management using encryption, SSL and OAuth
CONVAYR is fast, efficient and scalable with batching and use of bulk API